When I embarked on my first physical penetration test, I didn’t quite know what to expect. Sure, I had prepared for the task by planning out test cases and developing cover stories, but nothing beats the adrenaline of real-world execution. For the sake of protecting sensitive client information, I will refer to the client as "Fake Company".
Disclaimer: To respect the identities of the client and the pentesters, some of the images in this blog are manipulated with Photoshop and/or AI to remove any identifying information.
Day 0: Planning
Fake Company designs software solutions to streamline legal workflows for law firms, enterprises, and government entities. Their solutions help manage legal processes like litigation, investigations, compliance, and due diligence efficiently and effectively.
The scope of the physical pentest was simple: visit the client's corporate offices leased downtown and try to gain access to the 5th and 8th floors. The 5th floor is where Fake Company builds and maintains its software and digital products.
As part of the physical pentest, we were authorized by Fake Company to attempt to social engineer our way into their spaces with the ultimate goal of accessing any restricted areas and gaining physical control of secured systems.
Day 1: Laying the Groundwork
I was joined by my colleague - let's call him Mark. He and I started by observing. We set up in the lobby, close to the building's food court on the first floor. This public space gave us the perfect vantage point for passive reconnaissance, gathering information about the building's layout and security measures. Through our reconnaissance we identified which elevators to use, the location of the freight elevator, and the behaviors and patterns of security personnel.
Scoping Our Terrain
As part of the test, we were provided floor plans for the 5th and 8th floors. Upon reviewing the floor plan, we noticed that on both floors, the public elevators opened into a small vestibule. There were three points of entry on the 5th floor and 2 on the 8th floor. All points of entry were controlled by OpenPath badge readers. We witnessed employees using an app on their mobile phones to unlock the doors.

Next, we approached the loading dock security desk, posing as Fake Company employees that were planning to bring equipment over the weekend via the freight elevator. From the ensuing conversation, we learned three critical details:
- The building was staffed 24/7.
- A work order was required for equipment deliveries.
- The work order needed to be filled out by a Fake Company POC.
We obtained the building access request form via the building's public website; however, the form required a password. At first, we started by trying to brute simple passwords based on the street name, the building name, and a few other various permutations. Then, it dawned on us. Why not just ask for the password? A simple phone call to the property management company yielded the password to access the form submission site. Using a fabricated identity, we submitted a request for 5th-floor access. We were told upon submission of the form that we would get our access the next business day.
Additional Reconnaissance
After submitting our building access request, we decided to go back to the 5th floor and see if we could simply access the office space. To the client's credit, no employees allowed us through the doors. We saw a few employees returning from lunch and when we asked them to hold the door open for us, they asked us who we were and what we needed. We told employees we were there to meet with someone (we used the name of an employee we found on LinkedIn who we knew was not in the office), and the employees asked us to wait outside while they checked. We did not wait around for them to return to us.
We discovered several WiFi networks associated with Fake Company - all of which required authorization to access, including the FakeCompany-Visitor open network.
Day 2: Infiltration
The next morning, we visited the property management office to follow up on our request. They directed us to the security office, where we were handed an RFID key fob granting access to the 5th floor. The security office did not ask for us to verify our identities; they simply handed us the key fob that granted us access to the freight elevator.

Using a FlipperZero, we cloned the fob for backup—a small victory in bypassing traditional access controls.

With the fob in hand, we accessed the 5th floor via the freight elevator. While exploring the office space, we observed several security gaps:
- A rack meant for the storage of sensitive data was left unsecured.
- No idle workstations or devices were left unattended, indicating a strong BYOD policy.
- OpenPath entry controls secured the forensics lab and data room.

On a table within the office space were several shirts and sweaters donned with the company logo with a Post-It note stating "Free to a good home". Mark took one of these shirts and wore it, lending credibility to our presence on the floor.
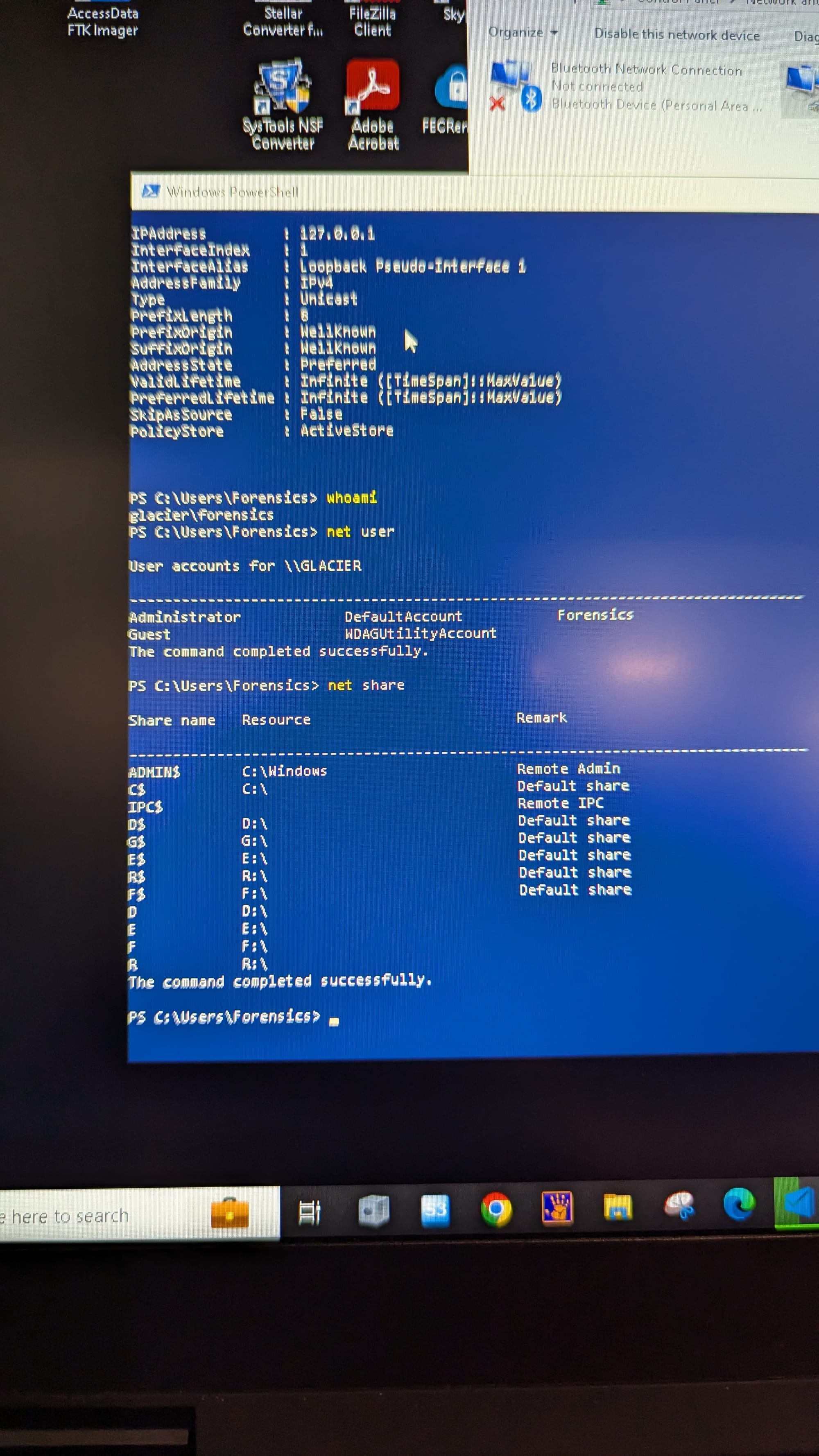
Despite the security controls in place, we managed to set up in a conference room and connect our laptops to an open desk. We were automatically joined to the internal network.
Despite these controls, we managed to set up in a conference room and connect our laptops to an open desk. We were automatically joined to the internal network.
Technical Reconnaissance
Using our own laptops and equipment, we setup at an empty desk on the floor. We connected one of the docking stations and were automatically joined to the network.
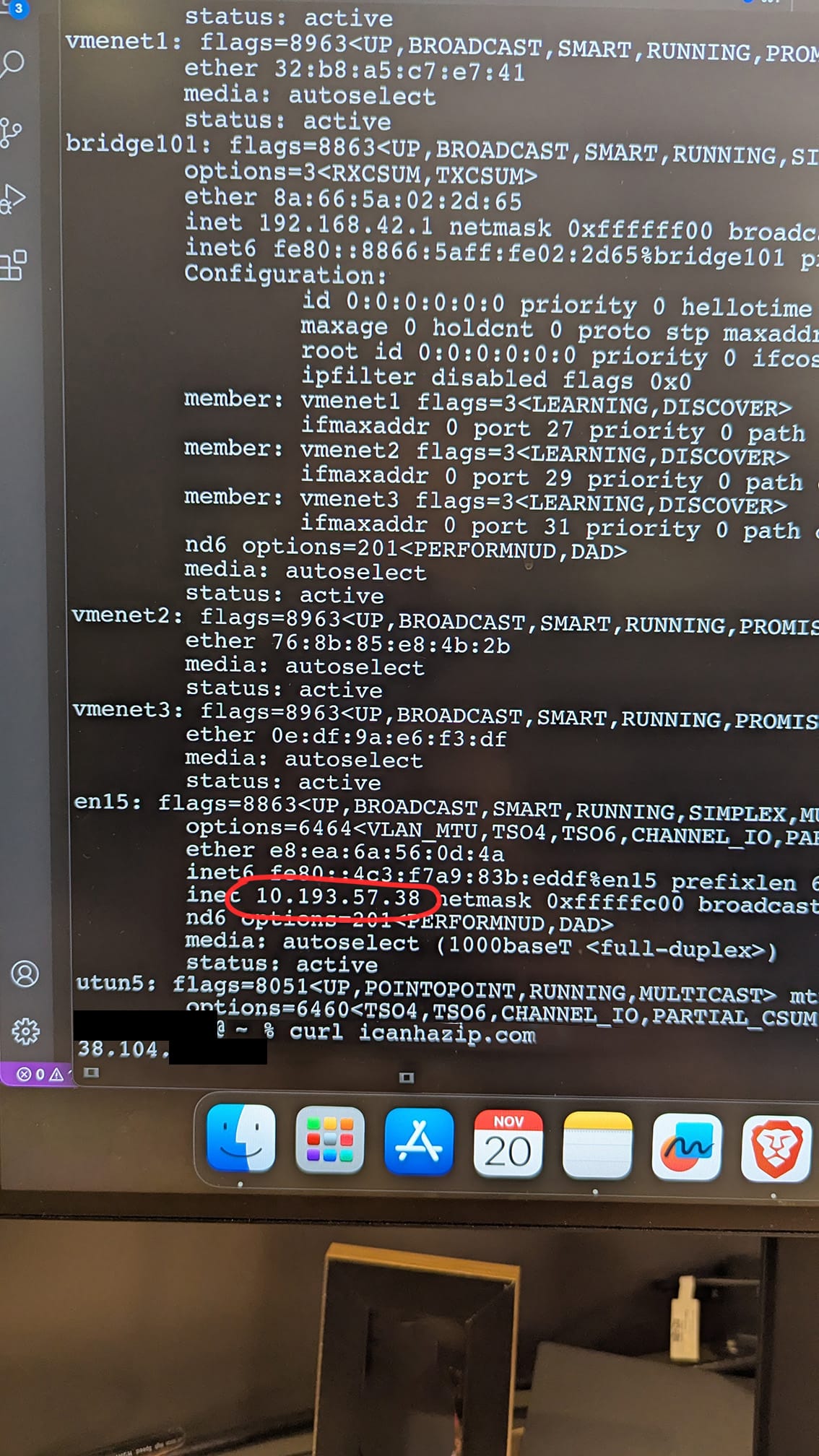
We executed an nmap scan to identify hosts on the network. Below is an example of the command used:
sudo nmap -sS -n -T4 10.193.58.0/24 -oX scan-fakecompany
The scan revealed a variety of devices, including those with open ports for services such as HTTPS, FTP, and Telnet. Identifying these was key to understanding potential network vulnerabilities.
Restricted Office
There were two areas of high interest for us during this physical pentest: The restricted office and the data room. Both rooms were secured using an OpenPath badge reader.
As Mark and I worked on enumerating the network, we noticed an employee going in and out of the restricted office. Whenever the door shut, there was about a 15-second delay when we would hear a clicking sound at the door, indicating an automated locking mechanism. So, we decided to wait.
After about an hour, we noticed the employee leave the lab carrying a water bottle and a bag - he was heading out for the day. So, after a few seconds, we entered the restricted office before the automated lock engaged - we had access to Fake Company's most sensitive room!
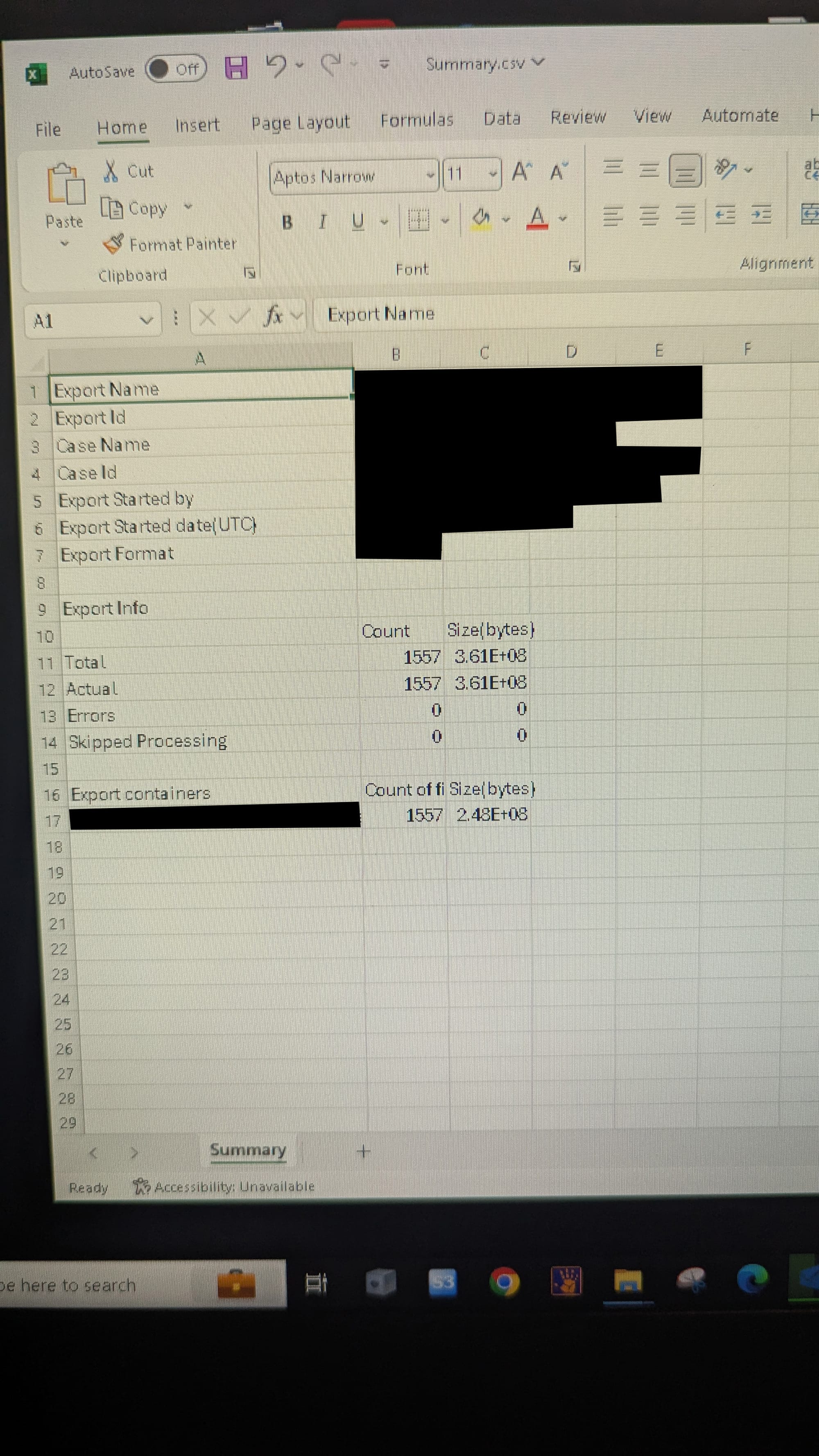
In this room, we found unsecured critical data and devices that were logged in and unlocked and a plethora of other sensitive things. At this point, we called our POC at Fake Company to give them an update - there was no need to break into anything else or establish persistence on any machines. After all, we discovered their most sensitive trove of information, and the fact that we got into this room was enough for our client.
Day 3: Expanding Access
On the final day, we pushed further. Although our initial request was for 5th-floor access, the same fob allowed us to access the 8th floor via the freight elevator. This oversight highlighted a lack of proper access segregation within the building.

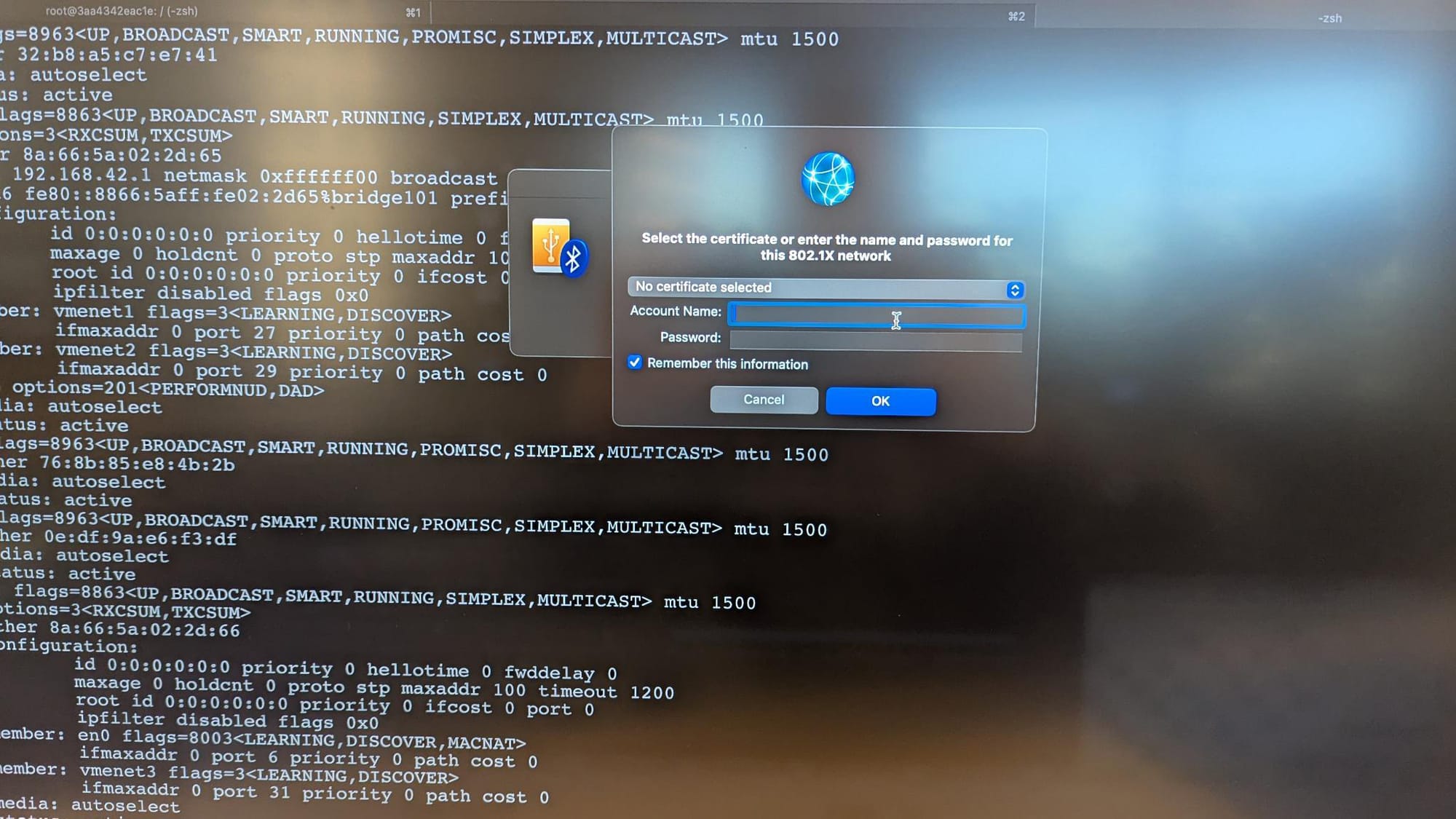
However, our attempts to connect to the network on the 8th floor were thwarted by an additional layer of security requiring a certificate or credentials.
Key Takeaways
- Social Engineering Wins: Human factors remain the most exploitable vulnerability.
- Physical Controls Matter: Relying on electronic security alone can leave critical gaps.
- Network Security Is a Must: While we accessed the 6th-floor network easily, additional layers of protection on the 9th floor showed stronger awareness.
Conclusion
This penetration test was a vivid reminder that effective security isn’t just about firewalls and passwords—it’s about bridging the physical and digital realms. Our journey through Fake Company’s offices demonstrated how seemingly small gaps, like an unsecured loading dock or lax access control practices, can serve as entry points for potential attackers.
Physical security is often an afterthought in cybersecurity discussions, but it plays a foundational role. If an attacker gains physical access to your environment, digital safeguards can quickly become irrelevant. Organizations must prioritize a comprehensive approach that integrates physical access protocols, employee training to mitigate social engineering risks, and robust network defenses.
The success of any security program lies in its weakest link, and in many cases, that link isn’t a piece of software—it’s a door left ajar or a friendly face eager to help. Strengthening physical security is an investment in ensuring that all other security measures can hold the line.
Let’s not forget: the best security is holistic security.

